Web Security is a significant concern for me. Over the past few years, I’ve been learning about ethical hacking and the broader field of web and server security and one topic that has always intrigued me is session hijacking.
While many security threats, such as weak passwords, SQL injections, and cross-site scripting (XSS), have been mitigated and are relatively easy to fix, session hijacking remains a persistent threat. Its ease of exploitation and potential damage make it a serious risk to web applications.
In this article, I’ll explain what session hijacking is, how it works, and how you can protect your web applications from this threat.
What is a Session?
To understand session hijacking, we first need to define what a session is. A session is a period where a user interacts with a web application. During this time, the user is authenticated and authorized to access certain resources. The session state is maintained by a session ID, a unique identifier generated by the server and sent to the client, usually stored in a cookie.
For example, in a Django application, the session ID is stored in a cookie named sessionid and looks like this: 1a2b3c4d5e6f7g8h9i0j. When the user sends a request, the session ID is included in the request headers, and the server uses this ID to identify the user and retrieve their session data. In Django, this can be done with the request.user object, which returns the currently authenticated user.
Without a session ID, the server wouldn’t be able to track the user across requests, requiring the user to log in again for every action.
What is Session Hijacking?
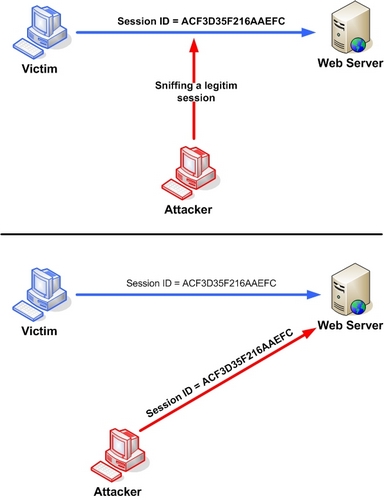
Now that we know what a session is, let’s define session hijacking. It is the act of taking over a user’s session by stealing their session ID. This can be achieved in several ways:
- Packet Sniffing: An attacker intercepts network traffic and captures the session ID if the connection is unencrypted.
- Cross-Site Scripting (XSS): An attacker injects malicious code into a web page that steals the session ID from the user’s browser, often using JavaScript to send the ID to the attacker’s server.
- Session Prediction: The attacker guesses the session ID by generating many possible IDs and trying them until they find the correct one.
These are just a few examples of how session IDs can be stolen. More sophisticated attacks exist, but the goal is always the same: take control of the user’s session and impersonate them without their knowledge.
Why is Session Hijacking a Big Deal?
Session hijacking is particularly dangerous because it’s relatively easy to execute and can have severe consequences, session hijacking doesn’t require complex brute-force attacks or sophistacted social engineering skills. Even with strong passwords and multi-factor authentication (MFA), an attacker can still take over a session and impersonate the user with minimal effort.
The problem is more prevalent than you might think, In 2022, SpyCloud reported over 20 billion records exposed in data breaches. While brute force attempts to guess a password would require bypassing rate-limiting, MFA, and other security measures, session hijacking sidesteps this, as the attacker is already authenticated.
Test It Yourself
To demonstrate how easy it is to hijack a session, try the following:
- Go to a website where you’re logged in.
- Open your browser’s developer tools and navigate to the “Application” tab.
- Locate the cookie containing the session ID and copy it.
- Open an incognito window and visit the same website.
- Paste the session ID into the cookie storage and refresh the page.
You’ll now be logged in as the user whose session ID you copied, showing how simple it is to hijack a session even with MFA enabled, in a real attack scenario, an attacker would use more sophisticated methods to steal session IDs, but the principle remains the same.
Session Hijacking Renders Other Security Measures Useless
In recent years, several security measures have been introduced to protect against various attacks, but session hijacking can bypass many of them:
HTTPS (TLS/SSL Encryption)
- Purpose: Encrypts communication between the user’s browser and the server, preventing interception of sensitive information like session tokens.
- Limitations: While HTTPS protects data in transit, it can’t prevent session hijacking if the session token is stolen through other means such as XSS.
Multi-Factor Authentication (MFA)
- Purpose: Adds an extra layer of security beyond passwords, making it harder for attackers to gain access to accounts.
- Limitations: MFA protects against unauthorized account access, but it can’t stop session hijacking once a session is established.
SameSite Cookies
- Purpose: Prevents session cookies from being sent with cross-site requests, reducing the risk of CSRF and XSS attacks.
- Limitations: SameSite doesn’t stop an attacker who has already obtained the session cookie.
Session Timeout and Inactivity Logout
- Purpose: Logs users out after a period of inactivity or at the end of a session, minimizing the window for hijacking.
- Limitations: If an attacker captures the session token before the timeout, they can still hijack the session.
Content Security Policy (CSP)
- Purpose: Restricts inline scripts and mitigates XSS attacks.
- Limitations: CSP helps protect against script injection but won’t stop an attacker who has already stolen the session token.
How to Protect Against Session Hijacking
Although it’s difficult to completely prevent session hijacking, you can take steps as a developer to reduce the risk:
- Use HTTPS Everywhere: Ensure your entire application is served over HTTPS to encrypt communication and protect against packet sniffing.
- Implement Secure Cookies: Use the
SecureandHttpOnlyflags on session cookies to prevent them from being accessed by JavaScript or transmitted over insecure connections. - Non-Predictable Session IDs: Use a cryptographically secure random number generator for session IDs, leveraging your framework’s session management tools.
- Implement Session Timeouts: Set reasonable session timeouts and log users out after inactivity or re-authenticate them periodically.
- Sanitize User Input: Prevent XSS attacks by validating and sanitizing user input—one of the most common ways attackers steal session IDs.
Conclusion
Session hijacking is a serious threat to web applications, especially since measures like strong passwords and MFA aren’t enough to protect against it. As a developer, following best practices and implementing the security features provided by modern frameworks can help mitigate the risk. As a user, understanding how session hijacking works will help you take steps to protect your sessions and data.